Data security policy
1.1 Introduction
Information systems containing data are valuable assets to Re-engage. Created from a range of sources including, but not limited to, staff, volunteers, older people, funders and donors, referrers, and organisations. Most of this data is personal but also includes confidential and sensitive business information.
As efforts to harness technology and transform operations increase the reliance on information systems, they become critical points of operational, regulatory, and reputational risk. Failure to protect information systems and their data can have a huge impact on the charity from a financial and reputational standpoint, which can severely impact our ability to deliver on our charitable objectives. Aspects of this policy overlap with the data protection policy to which reference should be made.
1.2 Aim
The aim of the Re-engage Information Security Policy is to preserve:
- Confidentiality: Access is restricted to those authorised individuals avoiding unauthorised disclosure and/or misuse.
- Integrity: IT systems remain accurate and complete, and systems operate to specification avoiding the alteration and/or damage to assets.
- Availability: Information is accessible and usable upon demand by authorised individuals avoiding destruction or inaccessibility of systems and assets.
- Security: Information receives the appropriate level of protection in accordance with its importance to the charity.
This policy defines controls and procedures to ensure that individuals with access to systems and information are aware of their responsibilities, roles, and accountability to ensure that we:
- Identify and understand security risks.
- Protect and safeguard services.
- Detect and monitor systems for anomalous activity.
- Respond and plan for disasters and incidents.
- Recover services that were impaired from security events.
1.3 Scope
This policy applies to:
- This policy applies to all charity employees, trustees, freelancers, interns, and corporate volunteers and anyone who should be given access to the charity’s IT systems.
- Information about individuals and / or evidence of the charity's official activities; whether collected, stored, used, accessed, shared, transported, retained, or deleted.
- Information systems operated by the charity that collect, store, process, disseminate, transmit, or dispose of information; including third-party information systems that connect to Re-engage systems. Information systems that may be entirely paper-based, computer based, or a combination of both; an information system is a system that incorporates all the processes needed to effectively manage data.
1.4 Awareness and training
Data governance training is mandatory. All employees are required to complete the on-line data protection training and an annual refresher.
1.5 Non-compliance
Any individual in breach of this policy could be subject to loss or limitations on use of information and information systems, disciplinary action, or dismissal.
1.6 Policies and procedures associated with this document
- Document management policy
- Data protection policy and privacy notice
- Register of systems
- Back-up and disaster recovery procedure
2. Roles and responsibilities
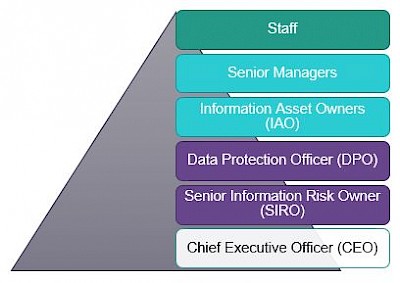
Some positions may be held by the same individual, and some may be held by more than one individual if there is a clear segregation of duties.
2.1 Responsibility
The board of trustees is ultimately responsible for information security and delegates this to the chief executive (CEO) at Re-engage. The CEO delegates this responsibility to the designated roles of senior information risk owner (SIRO) and data protection officer (DPO). The CEO, senior leadership team (SLT) and senior management team (SMT) are responsible for allocating resources and fostering commitment to information security across the charity.
2.2 Senior information risk owner (SIRO)
Is accountable for:
- Information risks and advises the Board on the effectiveness of data risk management across the charity.
- Ensuring that the charity’s employees are aware of their responsibilities and accountability for information security.
- The implementation and enforcement of the information security policy.
- Monitoring and reporting on the state of information security within the charity.
2.3 Data protection officer (DPO)
Is responsible for:
- Ensuring that data protection security principles for the handling of personal identifiable data are adhered to in relation to all information systems both manual and automated. And, for ensuring that employees and volunteers are aware of their responsibilities and accountability for information security.
- Auditing and conducting regular review of breaches and incidents across the charity, and reporting this to the Finance, audit and risk committee. Serious incidents are reported to the board of trustees in line with the serious incident reporting policy.
- Ensuring compliance with relevant legislation.
2.4 Information asset owner(s) (IAO)
The role of IAO typically applies to members of the leadership team but may also be assigned or shared with persons responsible for oversight of an initiative (service, project, or plan) that introduces, procures, modifies, or operates information assets (data or systems).
IAOs are accountable for ensuring that information systems under their control – and the colleagues that use them – operate in compliance with this policy and related laws.
IAOs are accountable for:
- Ensuring their system(s) operate in a manner consistent with legal and charity requirements.
- Ensuring their system(s) are compliant with required security controls.
- Categorising the sensitivity level of the information processed and stored in their system(s).
- Acting as business lead in response to security incidents and privacy breaches.
2.5 Senior managers
Senior managers are responsible for:
- Observing and reporting on the security of their team’s physical environments where information is processed or stored.
- Ensuring that all individuals under their charge, are aware of the information security policies, procedures, and their obligations therein.
- Determining the level of access to be granted to specific individuals.
- Ensuring individuals have access to appropriate training for the systems.
- Ensuring individuals know how to access advice on security matters.
2.6 Staff
Individuals that operate or have access to information or systems must comply with these security requirements, and ensure that the confidentiality, integrity, availability, and security of the information used is maintained.
Staff are responsible for the information being used, how it needs to be protectively handled, stored, and transferred ensuring:
- There is no intentional or unintentional compromise of any security measures put in place by the charity.
- There is no personal activity that results in, or causes risk to, the security of the information the charity holds.
Staff are also responsible for:
- Understanding the procedures, standards and protocols that exist for the sharing of information with others. Understanding how to report any suspected risk, near miss, or accidental or unlawful disclosure of restricted information within the charity.
- Understanding for raising any information security concerns with the information governance team.
3. Security controls
3.1 Acceptable use
Be sensible when using Re-engage’s IT resources, the resources are for you to do your work.
Always protect the resources, to help prevent unacceptable use and if the use would cause problems, upset, offence, or embarrassment, it’s probably not acceptable.
Context is important. Security risks can increase when working outside your normal workplace.
Be aware that your use of resources is monitored. During an investigation into a security incident, IT forensic techniques capture evidence. If you’re not sure if something is acceptable, ask for help first.
Above all, if you think there is a problem, report it or ask for help.
What is meant by IT?
IT means the devices or services you use for creating, storing, or sharing information. This includes everything from devices (such as laptops, ‘phones, mobile Wi-Fi hotspots (MiFi), iPads, tablets, printers, USB “memory sticks”) through to software and programs online.
Acceptable use of Re-engage IT
IT helps you complete your tasks as efficiently and effectively as possible and fulfil your role. As a Re-engage employee, you might need account details such as passwords to use the IT. Acceptable use also means protecting this kind of information.
Acceptable use can vary according to context. For example, checking sensitive personal details might be perfectly normal within a secured office, but is not acceptable in a public space or at home where someone other than you might be able to access sensitive data.
Unacceptable use of Re-engage’s IT
Unacceptable use of IT can hinder your ability to work, or is unlawful or illegal, or does not take the context into account.
There are many unacceptable uses of IT, making it impossible to provide a complete list. Examples of things to avoid include:
- Deliberately or accidentally sharing resources or information, such as passwords, with people who are not supposed to have them.
- Using resources without permission.
- Storing sensitive information where it could easily be lost or stolen.
- Using unapproved tools or processes to store sensitive information, such as passwords or credit card details.
- Using your work email address for personal tasks.
- Using your personal devices or your personal email address for work tasks.
- Excessive private use during working time.
- Installing unlicensed or unauthorised software.
- Sending your work material to your personal devices or your personal email accounts. (It is of course acceptable and necessary from time-to-time to send work material to someone else’s email address when they are directly involved with that work)
- Violating the privacy of others
- Accessing, downloading, or sharing offensive or indecent materials
- Infringing copyright, libelling, or defaming other persons using the business' email system
Why unacceptable use is a problem
Unacceptable use of IT might affect the charity in several ways, including but not limited to:
- Bad publicity or embarrassment.
- Increased or unexpected costs or delays.
- Civil or legal action.
- Reduced efficiency and effectiveness.
Unacceptable use might also affect you, too:
- Suspension of access, so that you cannot do your work.
- Disciplinary proceedings, up to and including dismissal.
- Termination of contract for contractors and agency staff.
Keeping control
You are responsible for protecting your Re-engage IT resources. This includes keeping your usernames and passwords safe and secure.
It also means looking after your equipment, especially when working from home or travelling for work. You are responsible for protecting any equipment issued to you. Any theft of, or deliberate or wilful damage to your equipment, should be reported immediately to your line manager and the director of finance and resources.
While you might be careful about acceptable use of your IT, there are still risks from malware, ransomware, or phishing attacks.
If you get an email from anyone or anywhere that you are not sure about, remember:
- Don’t open any attachments.
- Don’t click on any links in the email.
If there is any doubt, or you are worried that the email might be malicious or inappropriate, report it immediately as an IT security incident.
Personal use
Unless unavoidable, Re-engage IT equipment and software should not be used for personal use.
3.2 Data sharing agreements
Data sharing agreements with external third parties must be in operation before allowing access to Re-engage information systems and information. Agreements ensure that the employees or sub-contractors of the external organisation comply with all appropriate security policies. A non-disclosure agreement is be signed by any individual(s) given access to Re-engage’s systems.
3.3 Identification of assets and risks
3.3.1 Catalogue assets
SIRO/DPO establishes and maintains an information asset management process and associated systems register, in which:
- Each information asset (information systems and information) has a named information asset owner (IAO), who is responsible for the information security of that asset whether on premise or in the cloud. IAO(s) are responsible for ensuring regulatory and contractual compliance, as well as monitoring agreed use of the system.
- Maintenance of a register of all IT equipment. This includes the primary user, location, department, and serial number.
3.3.2 Identify vulnerabilities
Data and information flows are mapped to assess their privacy risks with regards to the type of data collected, the location of the data and who has access. The format it is stored, the method the data was collected, and who is accountable for it should also be examined.
A data protection impact assessment (DPIA) must be completed for processing that is likely to result in high risk to individuals (see DPIA Policy), to identify and access risks to individuals and identify any measures to mitigate those risks.
Vulnerability scans, looking for known issues, on all public-facing systems of and restricted systems are conducted on a regularly scheduled basis. Upon any configuration change to the system, an internal scan will be performed. Failed vulnerability scans must be addressed and followed by a retest, repeating these steps until the vulnerability testing completes successfully.
External and internal penetration testing, looking for exploitative weaknesses in systems, should be performed after any significant infrastructure or application changes.
3.3.3 Recognise supplier and partner risks
Contracts address obligations of third parties in relation to access, security, disclosure, retention, and disposal of the charity’s data before any work commences in accessing or handling personal data on Re-engages information systems.
We proactively monitor and review agreements with third parties to ensure that they cover all aspects of information security and data protection for existing activities.
3.4 Access and identity protection
3.4.1 Access Management
Individuals are not granted access to a live system unless properly trained and made aware of their security responsibilities.
The identity of the individual is verified prior to granting, changing, or re-enabling access to information systems by the line manager and/or IAO.
Access to information systems are controlled using unique user accounts, passwords and/or tokens. Except for service accounts, user accounts are uniquely assigned to named individuals, ensuring accountability and traceability. Individual access privileges may be temporarily disabled after the detection of unusual activity on the user account or failure to comply with access management and password management policies.
A principle of least privilege should limit access of users (including administrative accounts) to specific applications, data, and resources needed to complete a required task. Permissions may be elevated for a predefined time and purpose under agreement or supervision of the IAO. Where least privilege cannot be arranged due to technical limitations and access is necessary for legitimate need, then specific controls are in place to monitor actions whether physical or technical.
Administrative access to program libraries and technical configuration controls are restricted to authorised individuals who have a legitimate business need e.g., systems or database administrators and the director of finance and resources modifies/removes access privileges - as appropriate - when an individual changes job / leaves. The request to remove privileges is part of the charity’s onboarding / change / offboarding process.
Public or external accessibility is restricted to ringfenced areas of authorised systems, identified as such in the systems register.
Authorisation to use an application depends on the availability of a licence from the supplier. It is the responsibility of a system’s IAO to procure, hold, and issue licences for all software loaded on charity devices. Only charity-wide software will be centrally supported by the director of finance and resources and service desk supplier(s). Any software procurement must take place after approval of the SIRO.
3.4.2 Password policy (personal)
It is critical that strong authentication procedures / technology must be used for remote connections to the charity’s systems and use multi-factor authentication (MFA). Wherever possible, Re-engage adopts ‘password less’ authentication. Wherever private personal passwords are used, they should adhere to the following:
- Change default / initial passwords for systems and individuals
- Personal passwords must never be disclosed or shared with another person
- Azure AD password protection must be enforced to detect, and block known weak passwords and their variants, as well as weak terms that are specific to Re-engage.
- Passwords expiration: Contrary to common practice, Microsoft advises that password expiration requirements do more harm than good. Frequent expiration encourages users to select predictable passwords, composed of sequential words and numbers that are closely related to each other. In these cases, the next password can be predicted based on the previous password. Password expiration requirements offer no containment benefits because cybercriminals almost always use credentials as soon as they compromise them. This should not discourage intermittent expiration (annually, bi-annually, or when updating this policy) when also complimented by training to select a strong new password.
- Password complexity: Although combinations of uppercase, lowercase, numerals, and special characters significantly increases the integrity of a password; enforcing complexity requirements can also do more harm than good. Most people adapt to complexity restrictions in predictable ways, using patterns, for example, a capital letter in the first position, a symbol in the last, and a number in the last 2. Cybercriminals know this, so they run dictionary attacks using the most common substitutions, "$" for "s", "@" for "a," "1" for "l". It is better to create less complex, but longer and more memorable passwords
![Source: Whitney, L. (2022). How an 8-character password could be cracked in less than an hour. [online] TechRepublic. Available at: https://www.techrepublic.com/article/how-an-8-character-password-could-be-cracked-in-less-than-an-hour/.](/site/assets/files/84748/hacker_password_cracking.jpg)
Source: Whitney, L. (2022). How an 8-character password could be cracked in less than an hour. [online] TechRepublic. Available at: https://www.techrepublic.com/article/how-an-8-character-password-could-be-cracked-in-less-than-an-hour/.
- Password length: Simpler passwords with a greater number of characters are less vulnerable to cracking in a short amount of time. An 18-character password of just numbers would require three weeks to crack, but one with the same number of characters using lowercase letters would take 2 million years to crack. This shows why passphrases, which use a long string of real but random words, can be more secure than a complex but short password. This policy enforces a 14-character minimum, within the following guidelines:
- Do not use a password that is the same or like passwords you use on any other website: One of the most important precautions is to not reuse your primary Re-engage password anywhere else.
- Use more words: Don't use a single word, for example, ‘password’, or a commonly used phrase like ‘Iloveyou’. The key to a good passphrase is randomness — the words you use to create a passphrase should not have an obvious connection between them. A good passphrase example is ‘overripe-trekker-angular-envision-letter’, while a passphrase like ‘apple-pear-banana-orange’ would be much easier to crack. Find a combination of words you like by using a secure passphrase generator (such as Bitwarden).
3.4.3 Password policy (shared administrative accounts)
Shared administrative or service accounts must enforce the following:
- Sharing and storing: Passwords for shared accounts must be stored in a secure password management solution, that requires an individual to verify their organisational identity to obtain access.
- Password reset: Passwords for shared accounts are restricted from password reset facilities, instead requiring a password reset request to be raised with the IT service desk and approved by the system’s IAO.
- Password length and complexity: Passwords for shared accounts must use a randomly generated password of at least 20 characters; comprising a minimum of 5 each uppercase, lowercase, numerals, and special characters by using a secure password generator (such as Bitwarden).
- Authentication: Without exception, all shared administrative accounts (including ‘break-glass’ accounts) must be protected with multi-factor authentication. If a system is unable to support multiple people sharing multi-factor authentication tokens, then a shared account is not suitable.
3.5 Data protection
3.5.1 Transfer management (data-in-transit)
Re-engage sends restricted information – such as customer or employee data – between two parties over a secure transmission.
Secure and acceptable transmission methods are provided via Office 365, including: using Teams, SharePoint, or OneDrive to share links to select files and folders; or inviting guests into ringfenced collaboration areas within Office 365.
Insecure transmission methods such as email, phone, and fax should be avoided. Where efforts to introduce the recipient to receiving data by acceptable transmission methods has failed, or when a recipient insists on transmission by email; data files may be sent by email but only if they are password protected (see Password policy (personal)). Do not communicate the password by email; use another mode of communication to share the password.
Transferring information via unmanaged cloud-based services is prohibited unless the arrangement has been reviewed and agreed by the DPO, or SIRO. Examples include Google Drive, WeTransfer, iCloud, etc. Transferring information via physical media, such as USB hard drives, is prohibited
3.5.2 Storage management (data-at-rest)
- We secure physical records in paper format in storage when not in use. Do not leave physical records unattended on a desk.
- Digital records must be kept secure in managed information systems (such as Office 365) or databases (such as OPUS). Storing data in unsynchronised file locations (such as your computer’s desktop) is discouraged.
- Storing data in unmanaged systems (such as Google Workspace) is prohibited. Cloud storage must satisfy an adequate level of jurisdictional protection and security control. Where providers store data outside of the European Economic Area (EEA), additional contractual protection may be needed.
- Re-engage only stores data within the cloud space, on managed charity devices.
Information that is no longer required must be securely disposed of, in accordance with the retention periods outlined in the data retention policy. It is important to obtain permission before deleting any data.
Charity equipment capable of storing electronic data will be securely disposed of in line with IT security policies and WEE regulations and that certificates of destruction are obtained.
Deleted computer files are often sent to the ‘Recycle Bin’ or ‘Trash’, meaning that the files can be easily restored. Similar to files or documents on a computer, any emails deleted from the email inbox are usually not destroyed by default, as they are simply transferred to a ‘Deleted Items’ folder. These folders should regularly be emptied. If any paper records exist these should be disposed of by a secure method such as shredding.
3.6 Equipment and systems protection
3.6.1 Commitment to cloud
Re-engage is committed to cloud-based technology. This policy assumes all information systems continue to use cloud-based solutions and discourages adoption of physical infrastructure including central processors, networked file servers, and networking equipment in favour of virtual machines and cloud storage. Adoption of physical systems as a last resort prompts a review of this policy.
3.6.2 Configuration and change control management
The IT Department will establish and maintain baseline configurations and inventories of its network equipment and information systems throughout their life cycles and establish and enforce security configuration settings for them.
Changes to critical information resources must be reviewed, authorised, and tested prior to implementation and a formal log must be maintained of all change requests. Changes to information systems, applications or networks must be reviewed and approved by the IAOs responsible for those systems.
3.6.3 Computer equipment management
Charity devices such as a computer, mobile phone, laptop, or tablet will be kept secure and ensure that:
- The equipment is protected by a password or a PIN and, where available, encryption.
- The equipment has a supported operating system and software is up to date.
- The equipment is NOT lent to another person/member of staff.
- The user account and/or passwords or unlock codes are NOT revealed to anyone else.
- The installation of new software or hardware is NOT installed without authorisation by a member of the leadership team.
- Security software on the device is NOT changed or removed
- Patches or updates are NOT prevented from being installed.
- Restricted information is NOT stored on these devices.
- Charity devices will be handed back when no longer required in line with Re-engage offboarding process.
- Restricted information must be protected on all devices using security features provided for example secure print on printers or locking the device.
3.6.4 Removable media management
The charity does not allow the use of removable media.
Removable media includes but is not limited to:
- Flash drives
- USB keys
- Memory / SD cards
- Disks / CDs
- External hard drives
3.6.5 Patch management
The director of finance and resources, together with Acora One, is responsible for ensuring that any security-critical patches to internal operating systems or third-party software are installed onto assets on a regular basis.
Our IT partners are responsible for ensuring any security-critical patches to cloud based charity managed services are installed onto assets on a regular basis.
3.6.6 Malware and virus management
The director of finance and resources is responsible for installing and updating the Anti-Virus software in collaboration with Acora One. Virus databases will be updated on a regular basis on all managed devices. All devices connected to the charity network will automatically have anti-virus software loaded. Definition files will also be updated at least daily.
The charity and its IT managed service providers will use software countermeasures and management procedures to protect itself against the threat of malicious software.
3.6.7 Firewall management
Firewall filtering outbound and inbound internet traffic must be in place to mitigate the risks and potential losses associated with security threats to the charity network and information systems.
All installations, implementations, and modifications to the charity firewall and its configuration and ruleset are the responsibility of the IT provider.
3.6.8 Production / test environment management
Development, bug fixing, and testing in live production environments should be avoided.
3.6.9 Backup management
All central systems must have daily backup regimes formalised.
Removable backup media must be kept in a secure location away from the servers concerned and all backups must be held securely to prevent unauthorised access to its contents and tested on a six monthly basis to verify data integrity.
3.7 Detection of anomalous activity (audit logging)
Audit logs are maintained to investigate security incidents, monitor all use of charity resources, provide accountability for transactions, track system changes, and assist in detection of system anomalies.
An audit trail of system access and user data use will be maintained and reviewed on a regular basis. The charity will put in place routines to regularly audit compliance with this and other policies. In addition, it reserves the right to monitor activity where it suspects that there has been a breach of policy.
The charity reserves the right to monitor a member of staff’s usage of any IT system, including internet usage, and work-based communication records. Requests for monitoring must follow the disciplinary and grievance procedure and made in writing by the line manager to the HR manager.
Covert monitoring will only be carried out to investigate and evidence criminal activity or (gross) misconduct. Monitoring must comply with data protection law and regulation of investigatory powers act (RIPA).
The charity serves the right to retain information that it has gathered from staff use of the electronic communications systems for a period of one year and in the case of computer and internet use this includes the retention of date, time, name, and items accessed.
3.8 Breach response and recovery
3.8.1 Availability management (authenticity)
It is the responsibility of the director of finance and resources to ensure there is the ability to restore the availability and access to information in a timely manner in the event of a physical or technical incident where it has been identified as a business need.
3.8.2 Response
Security Incidents relating to the confidentiality or integrity of information must be managed in accordance with the Data Protection Policy. The severity of the incident shall be assessed, and the management response shall be proportionate to the threat.
Security Incidents relating to the availability of information must be managed in accordance with the Data Protection Policy. The severity of the incident shall be assessed, and the management response shall be proportionate to the threat.
Key information about serious Information Security incidents, including the impact of the incident (financial or otherwise), shall be formally recorded and the records shall be analysed to assess the effectiveness of information security controls.
New risks identified because of an incident shall be assigned to the relevant risk owner and unacceptable risks shall be mitigated promptly in accordance with the charity’s risk management processes.
3.8.3 Recovery
The charity recognises that some form of disaster may occur, despite precautions, and therefore must minimise the impact of such an event on its core business through tested disaster recovery plans.
The charity has a disaster recovery plan which is reviewed annually and updated, as necessary, to ensure it is applicable to the current environment and compliant with applicable policies, regulations, standards, and guidance.
The disaster recovery plan outlines the major activities the charity will perform to ensure it can maintain or resume operations within a reasonable time during and after a technological failures or information security incident. The plan should address how the charity will continue data processing if services, use, or access is disrupted for an extended period.
The policy in summary
In general, you must:
- Seek advice if you are unclear about any aspect of the information security policy
- Stay alert and report suspicious activity, or any loss or suspected loss of data
You must not:
- Engage in activity that causes risk – or results in harm to – to the security of Re-engage’s information systems and information the charity holds
- Undermine or seek to undermine the security of information systems
- Make copies of restricted charity information without permission
To protect your password, you must:
- Use hard-to-guess passwords that include different letter cases, numbers, and symbols
- Change your password if you have suspicion that it may have been compromised
- Password-protect sensitive files and devices with strong passwords including personally owned devices that access charity systems
You must not:
- Disclose your password to anyone or allow others to use your login or password
- Write down your passwords or enter passwords in front of others.
- Reuse your Re-engage password as the password for any other service
To protect your email, you must:
- Be cautious of suspicious emails and links
- Pay attention for phishing traps in emails
You must not:
- Open mail or attachments from an untrusted source
- Send restricted information by email unless it is encrypted and use the systems that you are told to use
To protect charity-issued devices such as laptops, tablets, and phones; you must:
- Lock devices when not in use by you
- Be mindful of the risks of using open (unsecured) Wi-Fi hotspots or computers in internet cafes, public libraries etc
- Protect all devices with the latest security patches, anti-virus/anti-malware software and firewalls.
- Encrypt mobile and portable devices and make sure that restricted information is always encrypted before it's sent to others
You must not:
- Leave your devices unlocked when left unattended
- Leave devices unattended in public
- Install unauthorised programs on your work devices
- Lend your devices to any another person
- Use charity devices to store restricted information or use personal devices to store any charity related data
To protect charity systems and data, you must:
- Only access data you are allowed to and
- Only save data to locations where the charity can access it
- Access data remotely using approved cloud systems
You must not:
- Transfer data outside of approved systems
- Provide access to charity information or systems to those who are not entitled to access
- Leave hard copies of restricted information or devices unattended or unsecured